What is IAM (Identity and Access Management):
Identity and Access Management (IAM) is a security service offered by AWS which allows you to manage user level access to AWS services and resources securely. You can create and manage AWS IAM users and groups to allow and deny access to AWS resources.
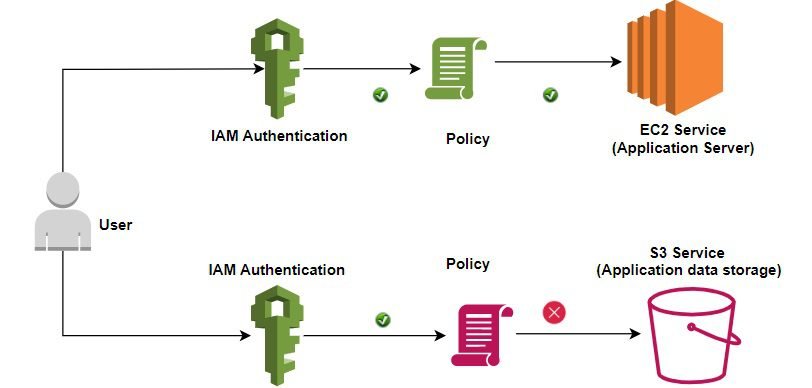
For example, a user allows to access EC2 service (Application server service) but deny to access S3 Service(Application data storage).
IAM: Components
- Users: An AWS IAM user is a unique identity with security credentials like a password or access & secret key. User is associated with permissions to control use of AWS resources. IAM User can be an individual person or application who needs access to another AWS Service.
- Groups: A group of collection of AWS IAM users. You can grant permissions to group using access control policies, Assigned permissions apply to all users belongs to that group. A user can be associated with multiple groups but a group can not be part of another group. Groups are helpful to categorize multiple responsibilities in an organization for example Admin Group, Developer Group, Support Group etc.
- Roles: AWS IAM role is a set of permissions to access AWS services. An IAM role is same as an IAM user that defines what is allowed and denied by an entity (User, application, or AWS service).AWS IAM roles are not associated with a group or specific user, Instead, it works based on temporary credentials/assume roles. Assuming a role means getting Security Token Service (STS) to provide you with a set of temporary credentials which are associated with the role and not with the entity that assumed the role.
- Policies: AWS IAM policies are associated with the AWS users, groups, and roles. It is a set of permissions and control access to AWS resources. Users, groups, and roles have no permissions by default. A policy is a JSON document with information about permissions such as:
- Who can access AWS resource
- Which AWS resources are allowed to access
- What actions are allowed and denied
- When AWS resources can be accessed.
Policy Example (JSON format)
{
"Version": "2012-10-17", //Version: specify the language syntax rules
"id": "server-permission", //Id: is as an optional identifier for the policy
"Statement": [ //Statement: is the main element for a policy
{
"Sid": "1", //Sid: statement Id is an optional identifier
"Effect": "Allow", //Effect: Grant permission (allow or deny)
"Principal":"*", //Principal: who can access it
"Action": [ //Action: What actions are allowed or deny
"logs:*",
"s3:*"
],
"Resource": [ //Resources: Specify AWS resources
"arn:aws:logs:us-east-1:*:*",
"arn:aws:s3::bucket/*"
]
}
]
}
AWS IAM: Features
- Centralize Control: AWS IAM Service allows you to manage centralized control of your AWS account. It means you can manage your AWS users, users’ security credentials, and their permission to access AWS resources.
- Shared Access: You can create a new user (with username and password) or modify existing user permission to delegate the responsibility of your role (i.e. Admin) without sharing your credentials.
- Granular Control: You can apply restrictions to different users for different AWS resource access. For example, you might allow users related to IT department can manage only EC2 service (i.e. your application servers) and users related to Database Team can manage only RDS services (i.e. your application database).
- Multi-factor authentication (MFA): You can use two-factor authentication for extra security checks. Two-factor authentication is a method of authentication where users must provide their credentials to work with account and also require a code from a configured device.
- Identity Federation: In case user is already registered and authenticated, such as in your corporate network or Facebook or Google or with any other internet Identity Provider- You can allow user to get access to AWS account using trust authentication method. This way helps user to maintain just one password to manage both accounts.
- Password Policy: AWS IAM allows you setup your own password policy using some configuration. For example, you can set password rules/patterns, expiry date, rotation policy, and no. of attempts allow before blocking the account.
- IAM Cost: It is free to use. There is no additional charge for creating Users, Groups, roles, and policies. Charges will be applied only to use of other AWS services by users.
- PCI DSS (Payment Card Industry Data Security Standard ) compliance: IAM complies/meet specified security standard for payment related industry requirements like processing, storage, and transmission of credit card data by a merchant or service provider.
- IAM can provide temporary access for User/Devices or services to use other AWS resources in your account.
IAM: How It works
- IAM Request: To access AWS (AWS Console, CLI, API) an IAM request sends to AWS by principal/user. Request context contains information:
- Actions or operations – The actions or operations that the principal wants to perform.
- Resources – The AWS resource object upon which the actions or operations are performed.
- Principal – Principal and their the policies that are associated with the entity that the principal used to sign in.
- Environment data – Information about the IP address, user agent, SSL enabled status or the time of day.
- Resource data – Data related to the resource like S3 bucket, file name, etc.
IAM: Best practices:
- Do not use your root user credentials for your daily work. Also, remove access key and secret key of root user. Create an individual IAM User for yourself as an Administrator to manage your work.
- Assign permissions at IAM group or role level instead of the individual IAM user level.
- Make a practice to regularly review your organization’s AWS IAM policies and grant least permissions to users.
- Try to use AWS managed Policies to assign permissions If possible.
- To manage your own custom policies use customer managed policy option instead of inline policy. It helps to manage your own custom policy in one place.
- Define a strong password policy for your users with some expiry date. Force user to change password after a certain time to make more secure your AWS environment.
- Use IAM roles for applications/resources that need to access other AWS resources.
- Monitor user, and last activity and removed unused user and credentials.
- Enable MFA ( multi-factor authentication)
- Do not share your credentials (password, access key, and secret access key).
Mastering AWS IAM: 10 Best Practices for Secure Cloud Management
