Difference between Security Group and Network Access Control List
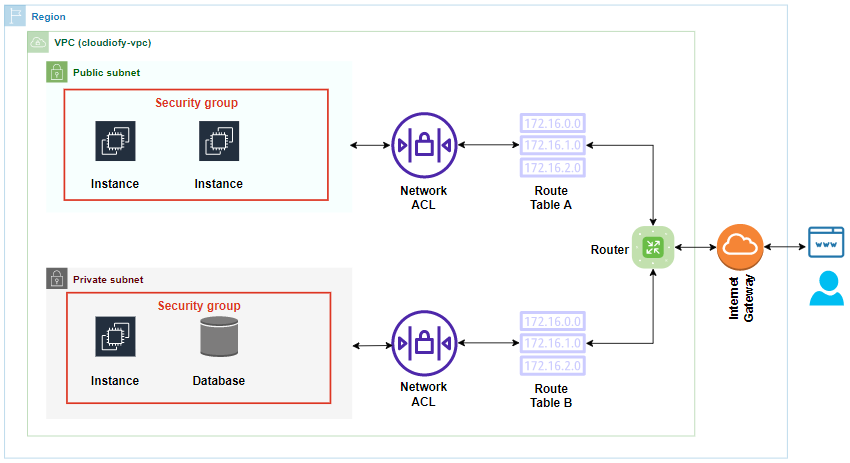
| Security Group | Network Access Control List |
| Security group is like a virtual firewall of EC2 Instances. It Operates at the instance level. | Network Access Control List is like a firewall of the VPC Subnets. It Operates at the subnet level. |
| Security group supports allow rules only (by default all rules are denied). We cannot block any specific IP address using SGs. | Network ACL supports allow and deny rules. We can block or deny any specific IP Address to establish a connection using NACL. |
| A security group is stateful: It means changes applied to an inbound rule, are automatically applied to the outgoing rule. For example, if we allow rule to incoming port 443 (standard port for HTTPS), outgoing will be automatically opened on port 443. | Network ACL is stateless: It means changes applied to an incoming rule will not be automatically applied to the outgoing rule. We need to explicitly allow the outgoing rule. |
| Security Group evaluates all rules before deciding whether to allow traffic. | Network ACL process rules in order, rule with the lower number gets processed first, when deciding whether to allow traffic. |
| It applies to an instance only if someone specifies the security group when launching the instance, or associates the security group with the instance later on. | It automatically applies to all instances in the subnets that it’s associated with (therefore, it provides an additional layer of defence if the security group rules are too permissive) |
| By default, we may add up to 5 AWS security groups per instance, but it is possible to use even more by making requests to increase limit from AWS support. | We can associate a network ACL with multiple subnet, however, a subnet can be associated with only one network ACL at a time. |
Difference between Security Group and Network Access Control List
